THREAT ASSESSMENT & RISK MANAGEMENT
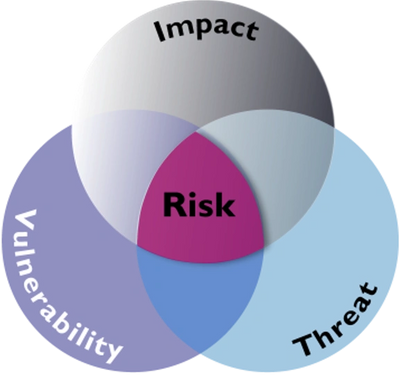
Threat Assessment is a process for evaluating and verifying perceived threats, including assessing their likelihood. In cybersecurity, a threat assessment is usually performed by security risk management and it precedes plans for mitigating threats against the enterprise.
The process of threat assessment begins with the initial assessment of a threat. It is then followed by a review of its seriousness, and creation of plans to address the underlying vulnerability (perhaps by sink holing or redirecting it). Finally, a follow-up assessment and plans for mitigation. In the last phase, if threats are both credible and likely, our security and risk teams use R-S-I-F indicators in their viability determination: Recency-Severity-Intensity-Frequency.
Threat assessments are normally done for predatory threats, ones that are offensive or targeted ones. This differs from a vulnerability assessment, which deals with affective threats, or ones that measure a target’s own defensive ability to respond to threats against it. Five (5) Steps to complete a successful Threat Assessment are:
1. Threat Determine the Scope of Your Threat Assessment.
2. Collect Necessary Data to Cover the Full Scope of Your Threat Assessment.
3. Identify Potential Vulnerabilities That Can Lead to Threats.
4. Analyze Any Threats You Uncover and Assign a Rating.
5. Perform Your Analysis.
Threat assessments aid our clients by proactively staying in line with information security requirements and best practices. Every business organization should be performing regular testing, but most do not have the resources, knowledge, independence or time to do so. They can leverage our experienced team to identify and eliminate weak points within their infrastructure to improve their overall security posture.
Red Team Operations
We attempt to compromise our client’s security as if we were a criminal carrying out nefarious activity. Basically, we do “bad” things to good people before the actual bad guys have a chance to cause damage.
Penetration Testing
Our penetration tests help assess, identify, and minimize (or eliminate) specific vulnerabilities within our client’s security infrastructure. Using ethical hacking, we attempt to infiltrate their organization based on predetermined parameters. The tests demonstrate susceptibility to attacks, and they inform which other specialized threat assessments might be needed to strengthen their security posture.
Purple Team Exercises
Using our Red Team operations as a basis, we work with our Purple Defensive Team to identify opportunities for improvement and implement new protocols and best practices to increase security posture.
Threat and Vulnerability Assessments
Our experienced team performs targeted testing to assess specific aspects of our client’s infrastructure or application and identify opportunities for improvement. We use a tailored approach that’s based on our client’s unique security needs to give the most meaningful, actionable results possible.
This website uses cookies.
We use cookies to analyze website traffic and optimize your website experience. By accepting our use of cookies, your data will be aggregated with all other user data.